DDoS attack on web servers – quick help from the specialist
One of my customers has been regularly hit with short DDoS attacks and load attacks for several weeks now. Recently, a large-scale attack has also been launched and has been ongoing for days.
The first attacks manifested themselves in short load peaks:
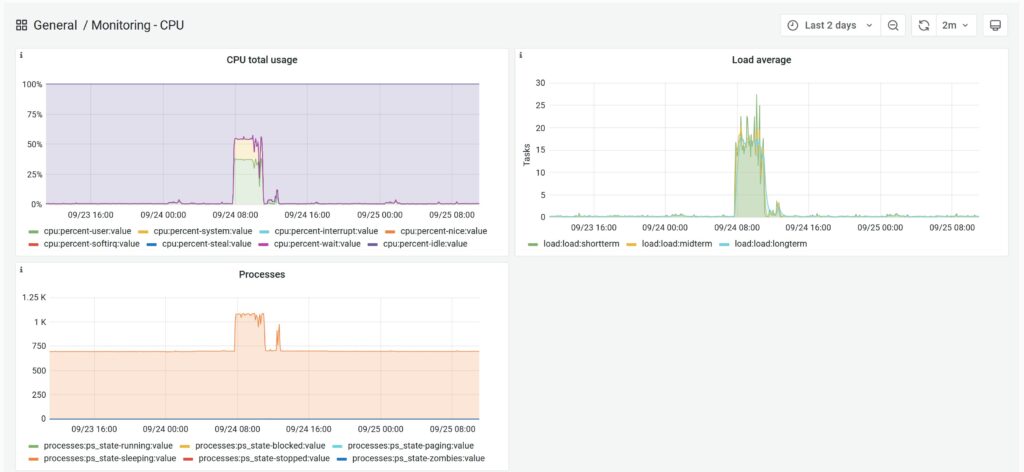
After that, the attacks occurred at intervals:
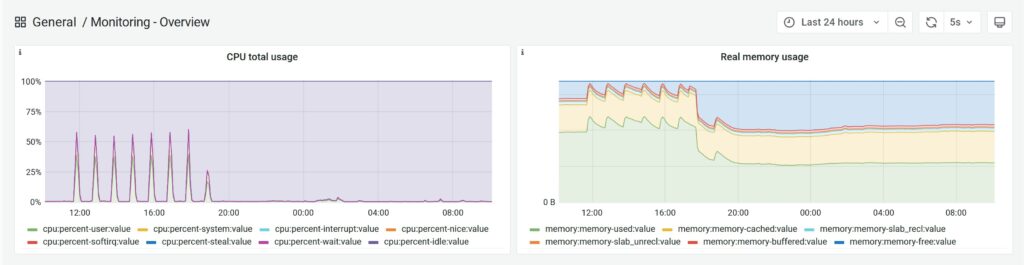
The graph above shows very clearly that we were still able to cope with the requests despite the size of the attack. However, there is a delay in page delivery during the peaks. This makes it more difficult for visitors to use the respective website and can also have a negative impact on search engine robots.
Even without actively fending off the attack, the web server I configured was already able to cope with the onslaught of visitors without any problems.
Furthermore, the attack takes place at intervals in order to disguise the persistence of the attack, so many website operators only become aware of the problem days later, as the website is not under permanent attack.
A combination of DDoS and normal calls was generated for the load. Apparently by an incredibly large botnet.
Blocking individual IP addresses or countries did not bring lasting success in this attack; just a few minutes later, the botnet recognized “the blockade” and simply used other computers from the network.
Of course, I was able to successfully fend off the attack for my customer. To do this, I used a combination of several methods available to me – which I cannot and do not want to discuss further here.
In addition to fending off the attack, we even used the attack to our advantage: During the attack, we allowed a subset to continue to access the client’s website. In the next step, we optimized our server environment for even larger visitor volumes (than we were already used to). We were thus able to reduce our memory usage by another 50% and close connections that were only kept open for a short time (as they are typically used in such an attack) even faster. As a result, we were also able to reduce CPU usage to a greater extent.
Note: Website operators normally pay for this artificial load
The attack on my customer is currently still being carried out, generating around 150 GB of traffic per day. Around 99% of the attack no longer needs to be answered by our nginx web server and is already filtered out upstream.
Is your website or store currently under attack and unavailable? I would be happy to help you at a reasonable hourly rate. Just write to me via my contact form.
In difficult cases, I am also happy to help with hosting websites that are actively under attack.